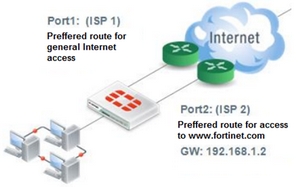
Birden fazla internet hattı kullanımlarında bazen belirli web adreslerine gidişlerde diğer internet hatlarının kullanılması gerekebilir.
Örneğin port1 ve port2 de iki internet hattımız olsun. genel internet trafiğimiz port1 de. Ama www.fortinet.com adresine port2 üzerinden erişmek istiyoruz.
Adımlar :
1 – IPS-URL-Filter için DNS tanımı
config system ips-urlfilter-dns
edit 208.91.112.53
next
edit 208.91.112.52
end
2- URL Filter cache yapılandırılması
config webfilter ips-urlfilter-cache-setting
set dns-retry-interval 1800
set extended-ttl 432000
end
3 – Gidilen URL adreslerinin otomatik olarak route tablosuna eklenmesi
config webfilter ips-urlfilter-setting
set device “port2″
set gateway 192.168.1.2
set distance 1
end
4- URL Filter listesi oluşturma
config webfilter urlfilter
edit 1
set name “UrlList”
set one-arm-ips-urlfilter enable
config entries
edit 1
set url “fortinet.com/FakeURLforWebfilter”
set action block
next
edit 2
set url “forti.net/FakeURLforWebfilter”
set action block
next
end
next
end
5 – WEB Profile Oluşturma
config webfilter profile
edit “URLsOverPort2″
config web
set urlfilter-table 1
end
next
end
6 – İnternet kuralı oluşturma
config firewall policy
edit 10
set srcintf “internal1″
set dstintf “port1″ “port2″
set srcaddr “all”
set dstaddr “all”
set action accept
set schedule “always”
set service “HTTP”
set utm-status enable
set webfilter-profile ” URLsOverPort2″
set profile-protocol-options “default”
set nat enable
next
end
www.fortinet.com adresinin IP adresi 66.171.121.44 dir. Routeing table listesine baktığımızda otomatik olarak port2 ye route edildiğini görürüz.
FGT60D (root) # get router info routing-table all
Codes: K – kernel, C – connected, S – static, R – RIP, B – BGP
O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, L1 – IS-IS level-1, L2 – IS-IS level-2,
* – candidate default
S* 0.0.0.0/0 [10/0] via 10.108.19.254, port1
[10/0] via 192.168.1.2, port2
C 10.108.16.0/22 is directly connected, port1
C 192.168.1.0/24 is directly connected, port2
C 10.158.0.0/22 is directly connected, internal1
S 66.171.121.44/32 [1/0] via 192.168.1.2, port2, [254/0]
Ayrıca sniff edildiğinde paketlerin geçiş arayüzü port2 olarak görünmekte.
FGT60D (root) # diagnose sniffer packet any “host 66.171.121.44″ 4 10
interfaces=[any]
filters=[host 66.171.121.44]
4.621420 internal1 in 10.158.2.66.50405 -> 66.171.121.44.80: syn 3734828542
4.621724 internal1 out 66.171.121.44.80 -> 10.158.2.66.50405: syn 4262438317 ack 3734828543
4.622091 internal1 in 10.158.2.66.50405 -> 66.171.121.44.80: ack 4262438318
4.622681 internal1 in 10.158.2.66.50405 -> 66.171.121.44.80: psh 3734828543 ack
4.622824 internal1 out 66.171.121.44.80 -> 10.158.2.66.50405: ack 3734829576
4.625467 port2 out 10.108.18.9.50405 -> 66.171.121.44.80: syn 28282687
4.817876 port2 in 66.171.121.44.80 -> 10.108.18.9.50405: syn 3871582676 ack
4.818094 port2 out 10.108.18.9.50405 -> 66.171.121.44.80: ack 3871582677
4.819637 port2 out 10.108.18.9.50405 -> 66.171.121.44.80: psh 28282688 ack
5.014052 port2 in 66.171.121.44.80 -> 10.108.18.9.50405: ack 2828372110 packets received by filter
0 packets dropped by kernel
11,284 total views, 1 views today