Bu makale FortiGate birimi ve kullanıcı kimlik doğrulaması için bir RADIUS sunucusu kullanarak FortiClient yazılımı ile FortiOS v5.2 ve v5.4 sürümünde IPSec VPN çevirmeli bağlantının nasıl yapılandırılacağı açıklamaktadır.
FortiGate (FortiOS v5.2 and v5.4)
FortiClient (Version 5.4)
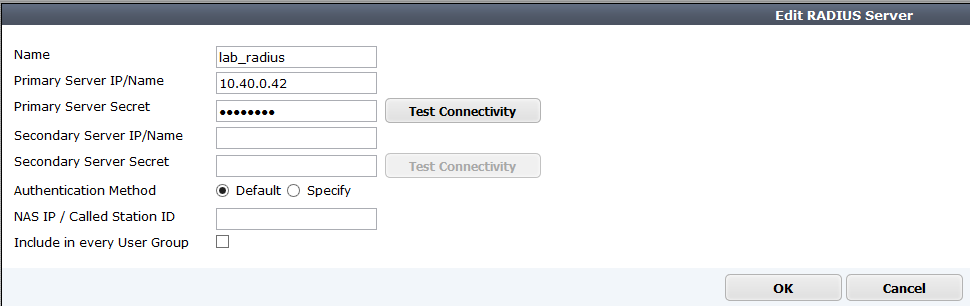
Fortigate v5.2 Radius Server Tanımlanması
User & Devices > Authentication > Radius Server > Create new >
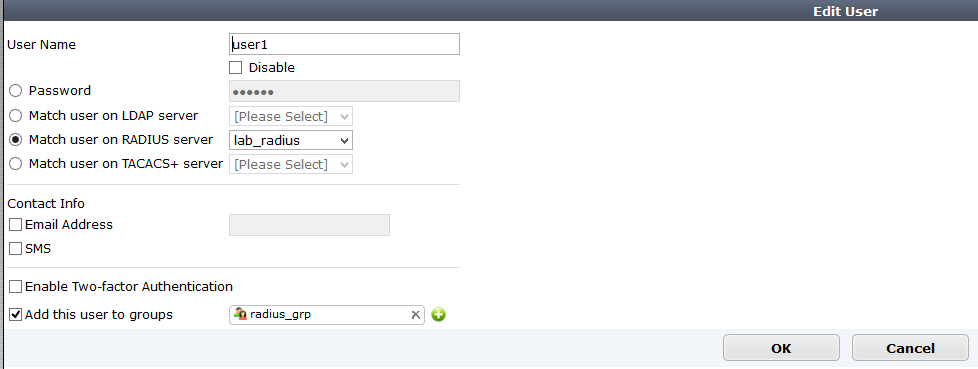
Lokal kullanıcı bölümünden bir kullanıcı açarak daha önce oluşturulan radius grubuna üye yapılır.
Not: Kullanıcı radius tipinde açılmalıdır.
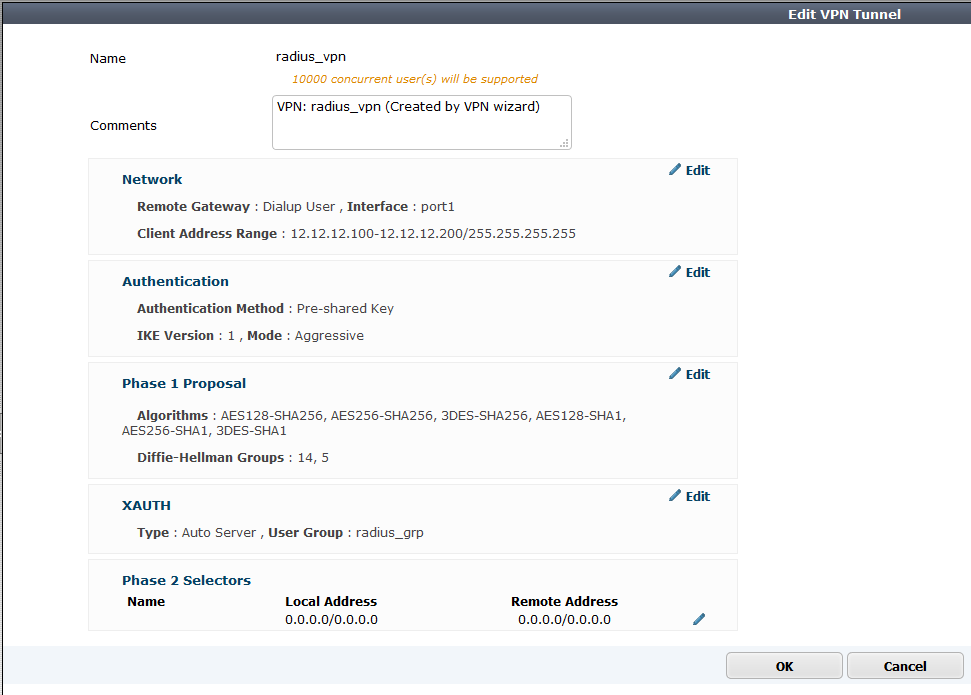
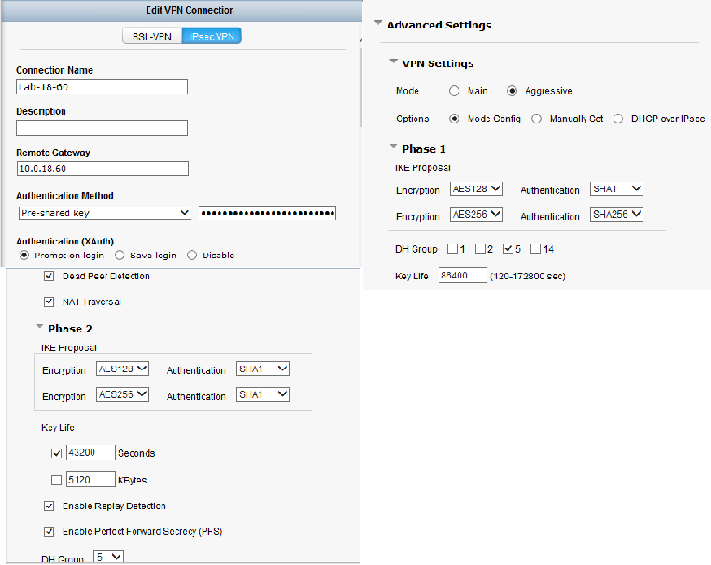
Dial-Up VPN Tanımlanır.
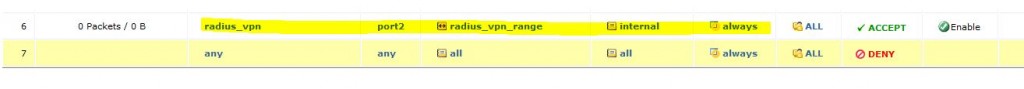
Sonrasında oluşturulan radius_vpn sanal interface inden lokale doğru kural açılır.
FortiClient Ayarları
Dial-VPN in debug edilmesi.
diag debug disable
diag debug reset
diag debug application ike -1
diag debug application fnbamd -1
diag debug enable
ike 0:radius_vpn_0:15: initiating XAUTH.
ike 0:radius_vpn_0:15: sending XAUTH request
ike 0:radius_vpn_0:15: enc F1D18748E306B7C8F5D921E906A1E94008100601AD2CF162000000540E000024788105BF21E64E429A7A060AFA8147587F3C2A0B286F800A56D1B16C0C43436A0000001401000D8CC088000040890000408A0000
ike 0:radius_vpn_0:15: out F1D18748E306B7C8F5D921E906A1E94008100601AD2CF1620000005CC419AD9E221E4E3A88909200FF38336B0FC4742159F4F0E2DA821A2B2EE2E28CAD2A3185A2E41DC541D80CB3C96F87BB44E389AC749A17D5CE2A379A013F8BB1
ike 0:radius_vpn_0:15: sent IKE msg (cfg_send): 10.0.18.60:500->172.26.73.110:500, len=92, id=f1d18748e306b7c8/f5d921e906a1e940:ad2cf162
ike 0:radius_vpn_0:15: peer has not completed XAUTH exchange
ike 0: comes 172.26.73.110:500->10.0.18.60:500,ifindex=2….
ike 0: IKEv1 exchange=Mode config id=f1d18748e306b7c8/f5d921e906a1e940:ad2cf162 len=108
ike 0: in F1D18748E306B7C8F5D921E906A1E94008100601AD2CF1620000006CC19AB6F8C5D0BD4519B8681CBCA886EEE796BD94D72DA5158AF36D2F06F39591CEBE1B0B1C720294D068DA16A02EF1437BEC37EDFE08571D6CFA9A4A9A290C7B2620A1EDF30695482C0D4EBF81734E50
ike 0:radius_vpn_0:15: dec F1D18748E306B7C8F5D921E906A1E94008100601AD2CF1620000006C0E000024055C850F6080371AED9A31A61CBD292F70F7D4944178C5E6A44B3B464FB4BAF90000002102000D8CC0880000408900057573657231408A00087040737377307264BBA9D0B6BC9DE5DA8BC10A
ike 0:radius_vpn_0:15: received XAUTH_USER_NAME ‘user1′ length 5
ike 0:radius_vpn_0:15: received XAUTH_USER_PASSWORD length 8
ike 0:radius_vpn_0: XAUTH user “user1″
ike 0:radius_vpn: auth group radius_grp
ike 0:radius_vpn_0: XAUTH 1571178739 pending
fnbamd_fsm.c[1890] handle_req-Rcvd auth req 1571178739 for user1 in radius_grp opt=00000000 prot=5
fnbamd_fsm.c[336] __compose_group_list_from_req-Group ‘radius_grp’
fnbamd_pop3.c[573] fnbamd_pop3_start-user1
fnbamd_cfg.c[500] __fnbamd_cfg_get_radius_list_by_group-Loading RADIUS server ‘lab_radius’ for usergroup ‘radius_grp’ (6)
fnbamd_radius.c[1060] fnbamd_radius_auth_send-Compose RADIUS request
fnbamd_auth.c[2260] fnbamd_auth_handle_radius_result-Passed group matching
fnbamd_fsm.c[867] find_matched_usr_grps-Group ‘radius_grp’ passed group matching
fnbamd_fsm.c[868] find_matched_usr_grps-Add matched group ‘radius_grp’(6)
fnbamd_comm.c[169] fnbamd_comm_send_result-Sending result 0 for req 1571178739
fnbamd_fsm.c[565] destroy_auth_session-delete session 1571178739
ike 0:radius_vpn_0:15: XAUTH 1571178739 result 0
ike 0:radius_vpn_0: XAUTH succeeded for user “user1″ group “radius_grp”
4,673 total views, 1 views today